So, I am sure most of you have been there. You just downloaded this great little free app from freeware heaven, clicked “next” through the series of endless disclaimers and dubious EULA’s, and have now watched the progress bar hit 100 per cent.
You fire up the new program and notice that it has now executed IE at the same time and has brought you to a page telling you that your system is infected. Damn, Damn Double Damn….haven’t I been down this road before?
Well, at least it didn’t lie. Your machine truly is infected and the longer it stays this way, the worse off you’ll be.
Malware is more than a nuisance though; it is an honest-to-god security threat and any real computer professional will give this class of software the prudent respect it deserves. Malware costs the world billions of dollars in lost productivity and is responsible for an unimaginable amount of identity theft and fraud. You may be inclined to chuckle at the colourful new icon that has been magically installed in your system tray, but this truly is no laughing matter.
Luckily, there are a ton of good tools out there that can deal with Malware reasonably well and are freely available. This article isn’t about recommending any of them (although I will plug an excellent product called Combo Fix recommended to me by Kevin, one of my co-workers) but rather this is for the unfortunate souls that have already run a program only to see that their malware is still alive and well.
So, where do we start. Sometimes malware can be ridiculously easy to spot. Simply opening the task manager will show you a process that you know shouldn’t be there and allow you to terminate and remove it. Then opening up MSCONFIG and disabling/deleting the startup item stops it from ever coming back. Great! But this does sound too easy, doesn’t it.
Modern malware almost never lends itself to easy removal and if it did, that nifty little program you downloaded to cleanse your system would have grabbed it anyway. Malware nowadays usually consists of several parts/processes and these processes work together to ensure that when one process is terminated, the other will fire it right back up. This is a cat and mouse game that you will not win using standard Windows management tools.
What I recommend doing, is downloading process explorer from Sysinternals. This tool will be invaluable in your fight against rogue software and will give you the weapons you’ll need to be victorious. Download Here.
Open up process explorer and you will now be privy to all sorts of system information that task manager doesn’t have (although the Windows 7 task manager is greatly improved).
Now look for processes that look unusual. Watch how your system behaves and look for processes that suddenly appear in the list when the malware itself executes. By default, these will be highlighted green and easy to see.
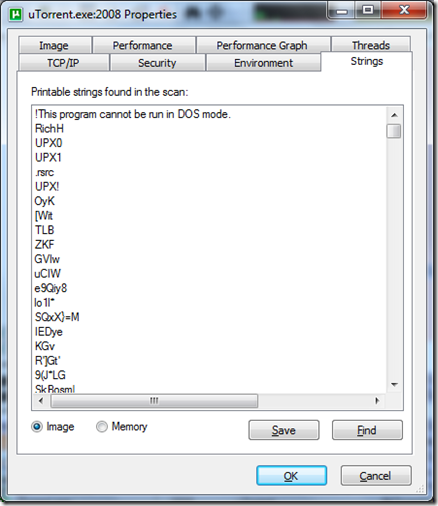
Now, when you find something unusual, double click on the process and go to strings tab. Look for something in there such as .com since most malware out there is designed to make some sort of a connection to a website to steal information or redirect your browsing experience in some way. Use your best judgement – if it is pointed to www.blackhathackerz.com that might be a clue that this file should not be there.
Once you have found your suspect exe file, do not kill it. Instead right click on it and suspend the process. This will prevent the other parts of the malware from restarting it as the program is still loaded in memory but just suspended and not terminated. Go through and suspend all of the suspect processes that appear. Then, once you are sure that you have got them all. Terminate them. (make a note of where they are located first in the environment tab in process explorer.)
Now, simply go through and delete the files off of your disk and clean up any registry entries that the product may have made. Use msconfig to disable any additional startup locations. Remember always export your registry and keep it safe before modifying your registry in any way.
Manually removing spyware doesn’t have to be painful. Nevertheless, some malware is going to involve a lot of work to track down on your part, but you will find that in time you will become more proficient at it and be able to clean machines up very quickly.
Last piece of advice, however. If you find yourself dealing with a root kit please disregard all that you have learned here today. There really is no way of trusting any machine that has been infected with a rootkit and your best bet is to just format windows and reinstall the OS.
I hope that this little tutorial helps!
Cheers.